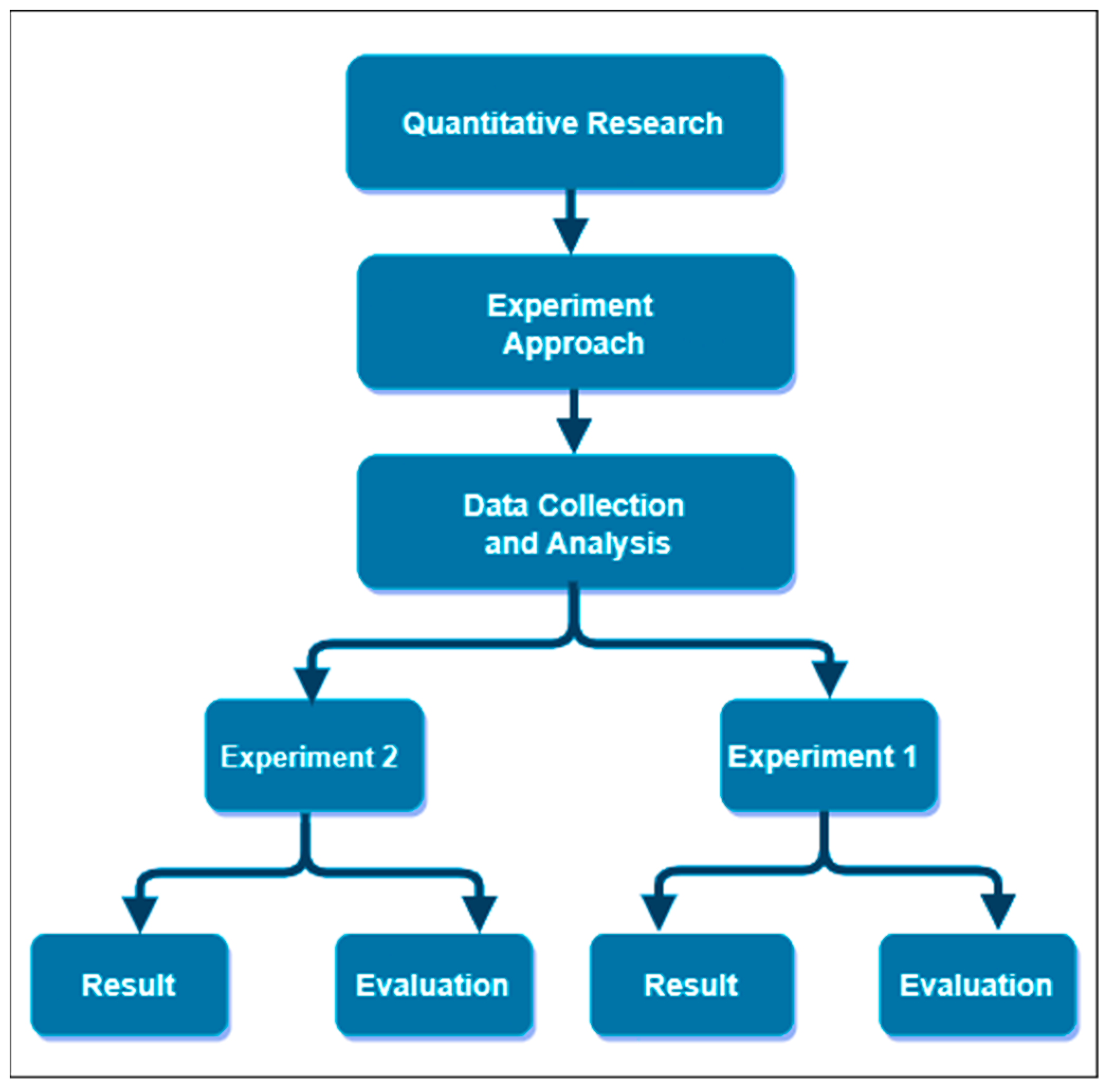
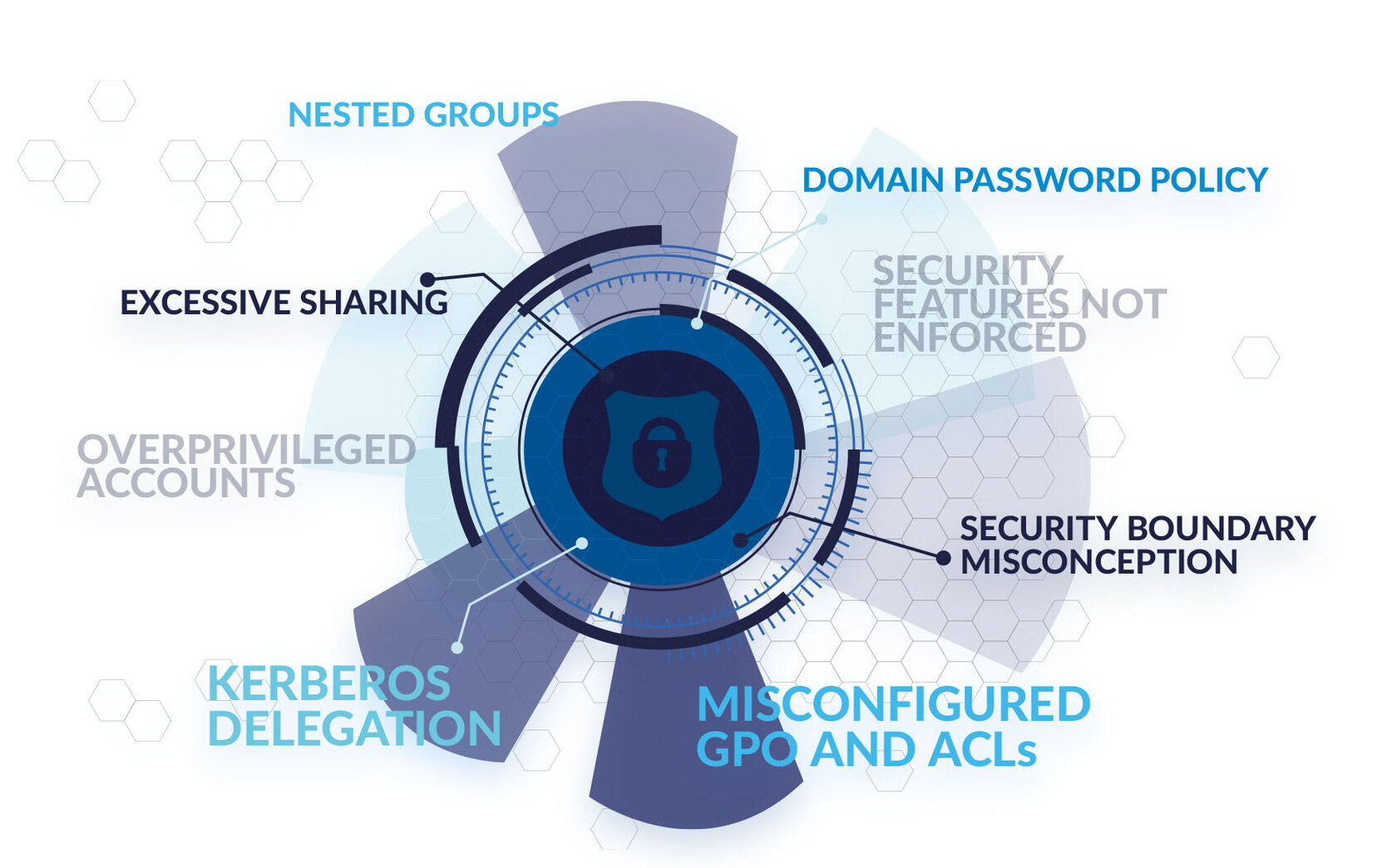
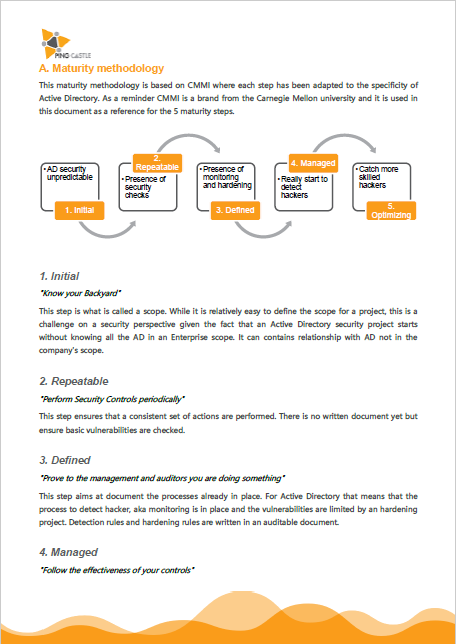
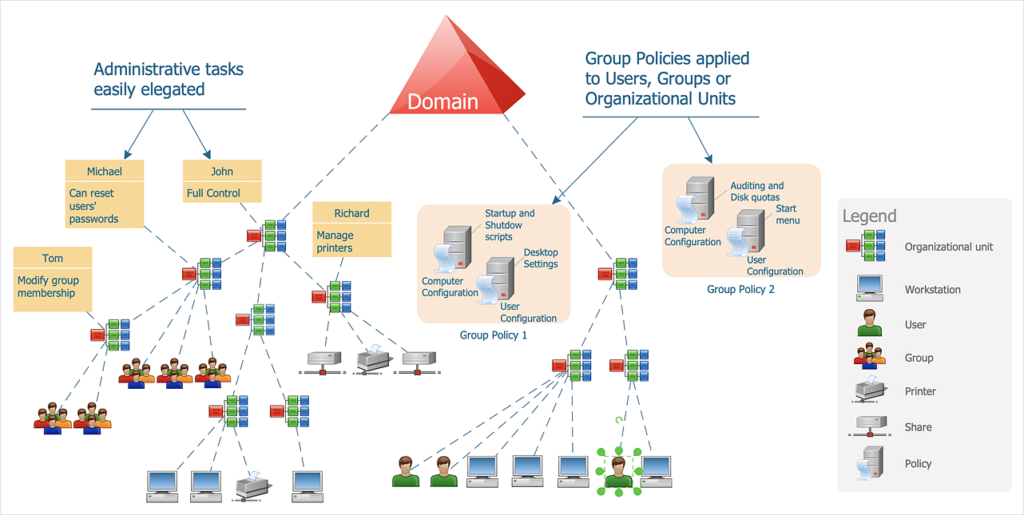
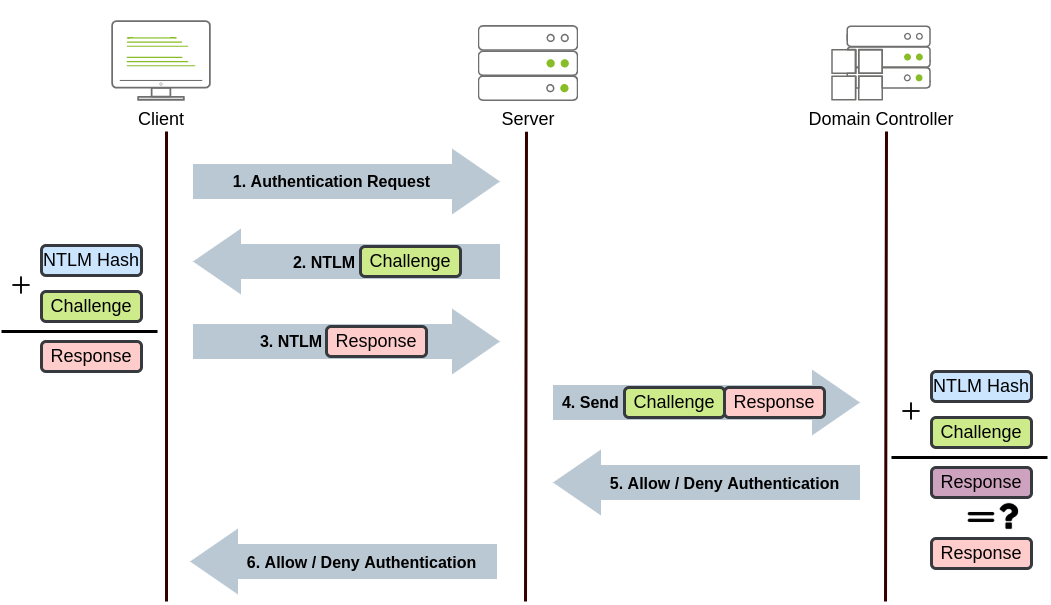
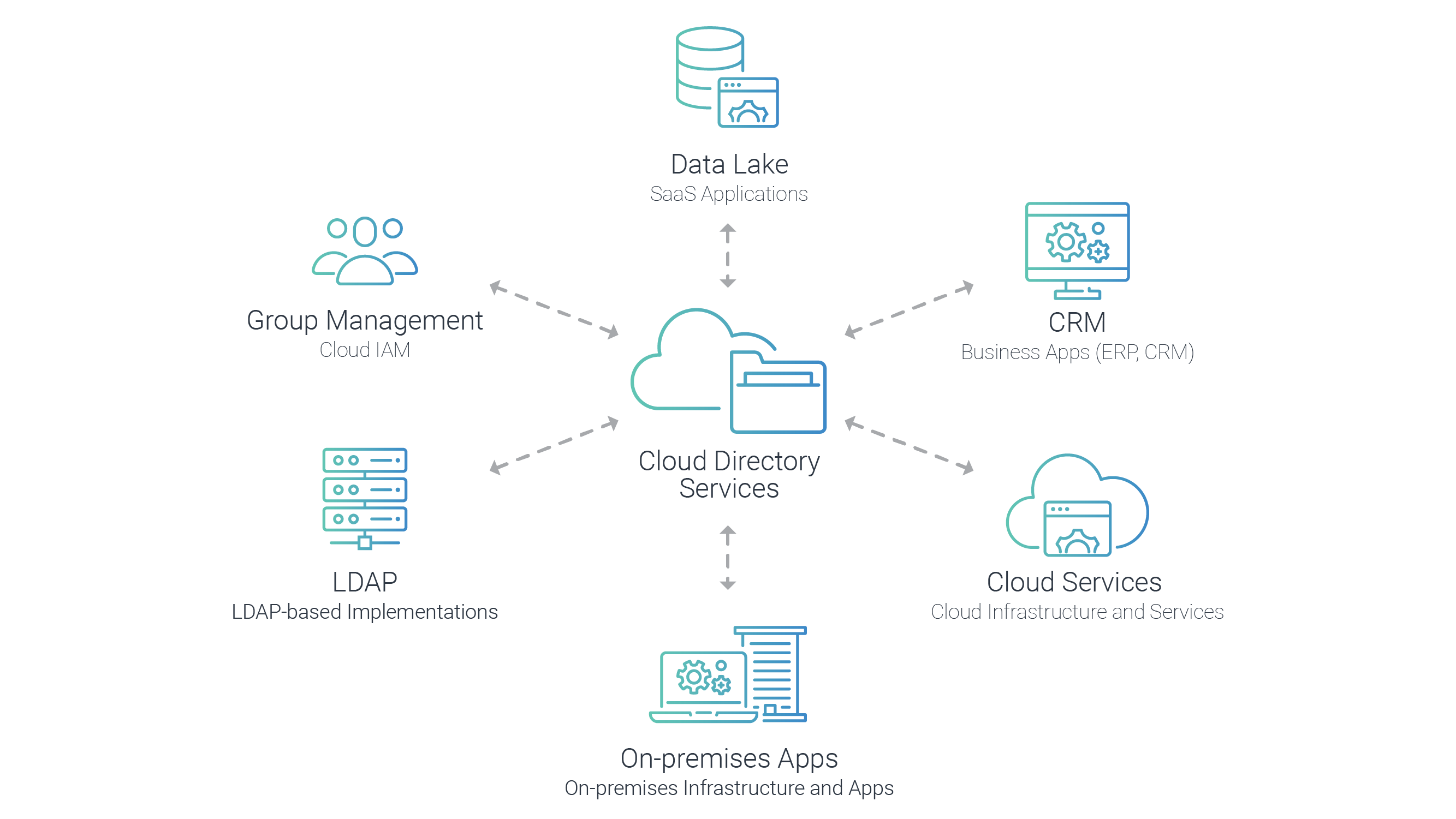
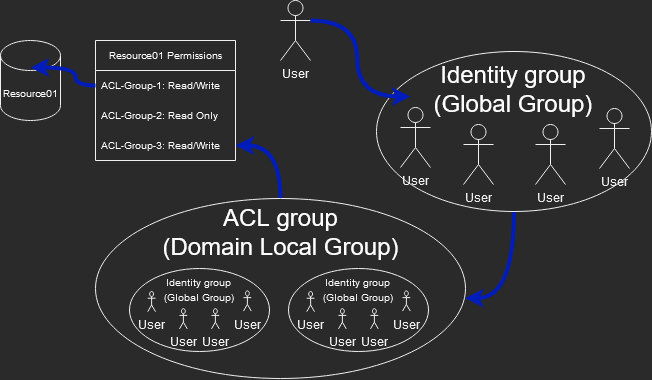
GitHub - Integration-IT/Active-Directory-Exploitation-Cheat-Sheet: A cheat sheet that contains common enumeration and attack methods for Windows Active Directory.
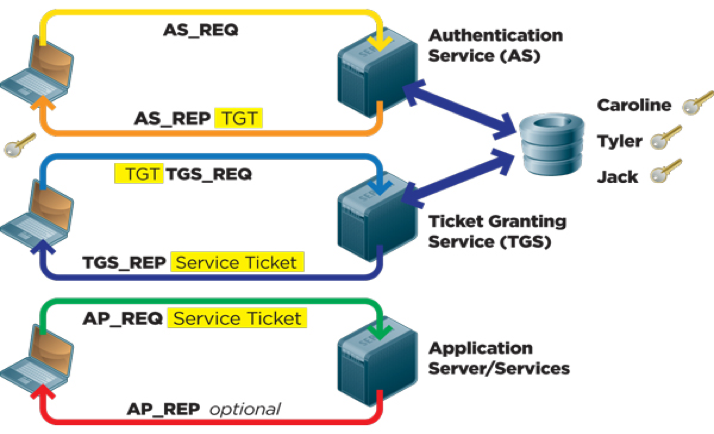
Exploring, Exploiting Active Directory Pen Test - Penetration Testing and CyberSecurity Solution - SecureLayer7