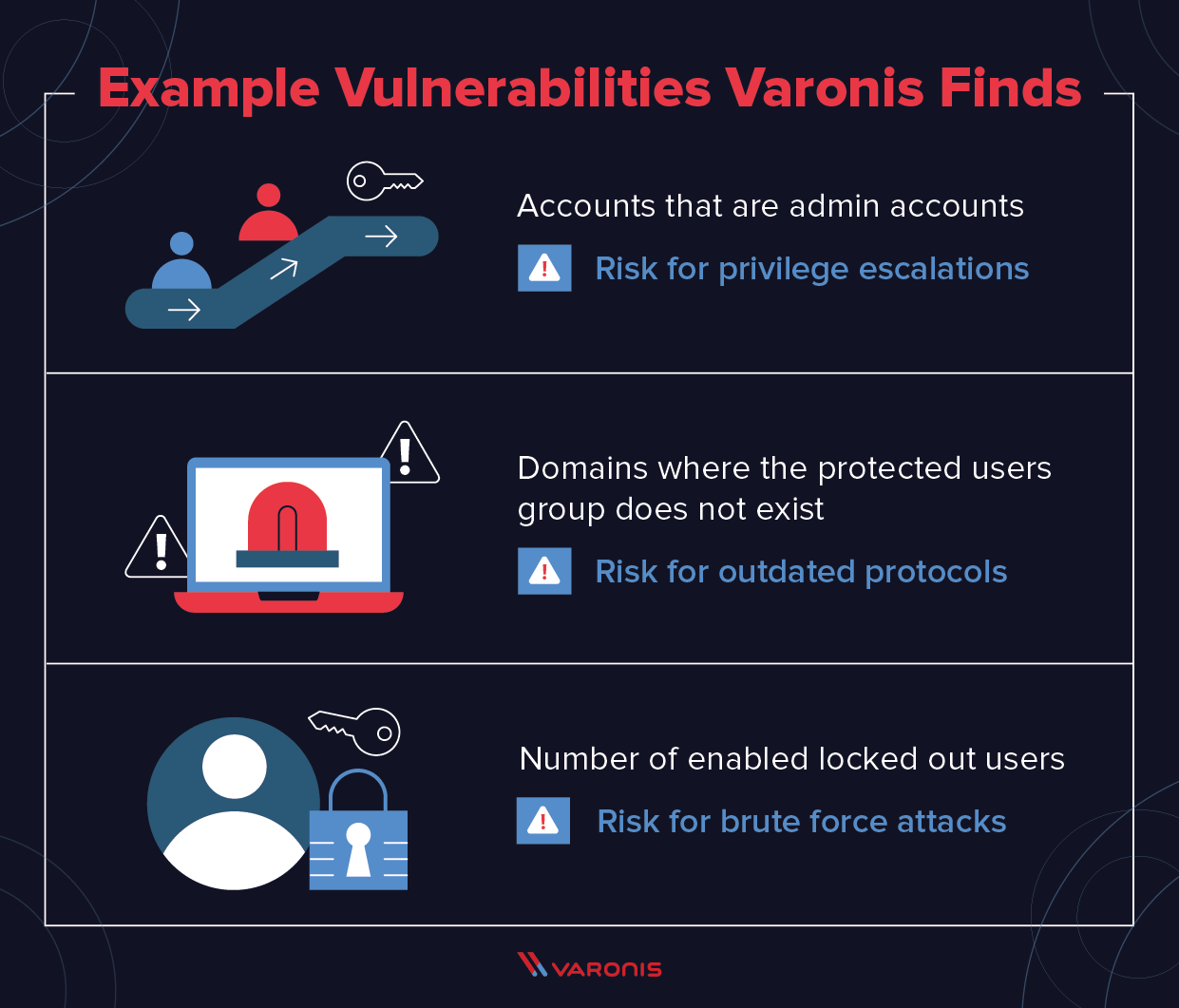
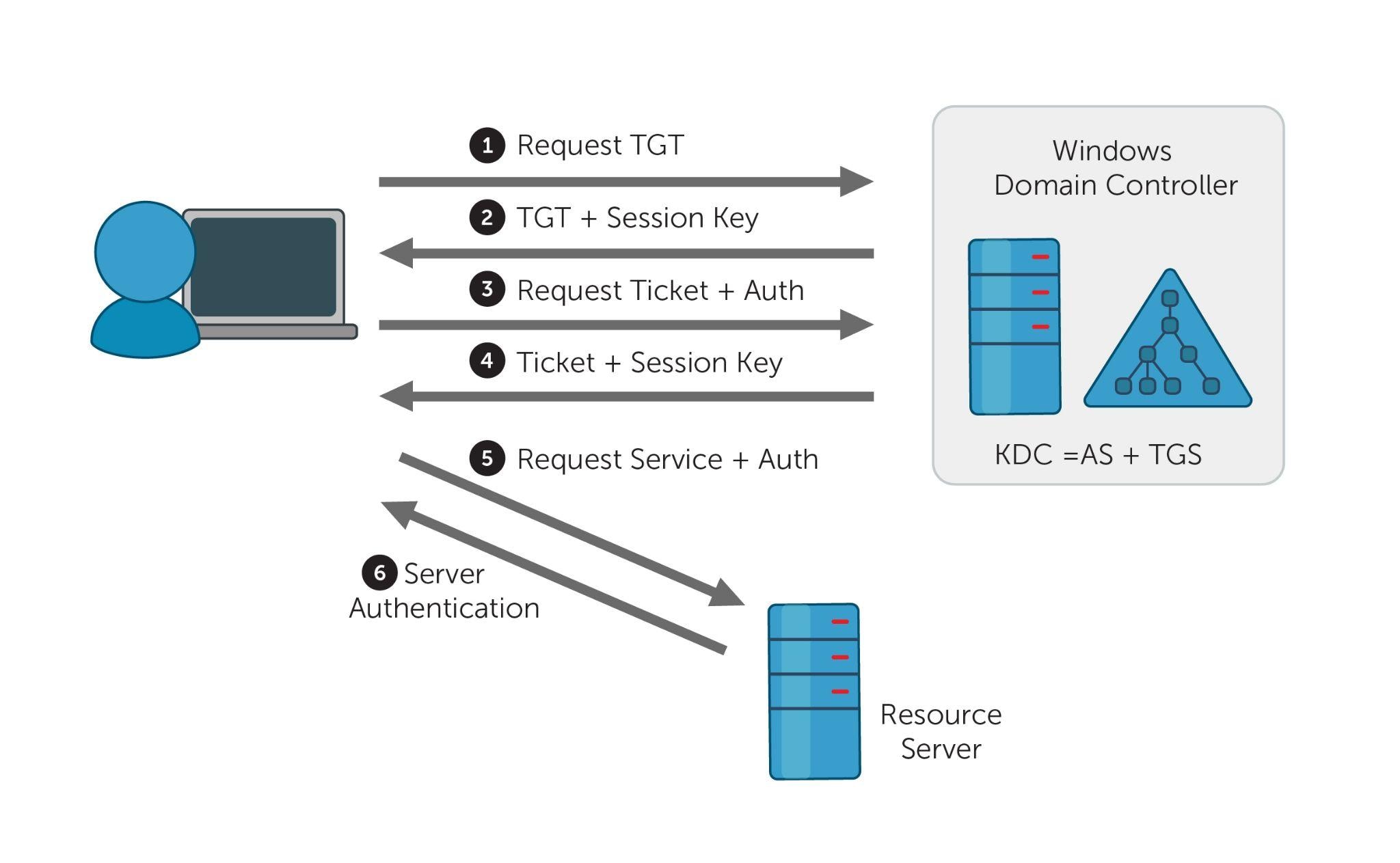
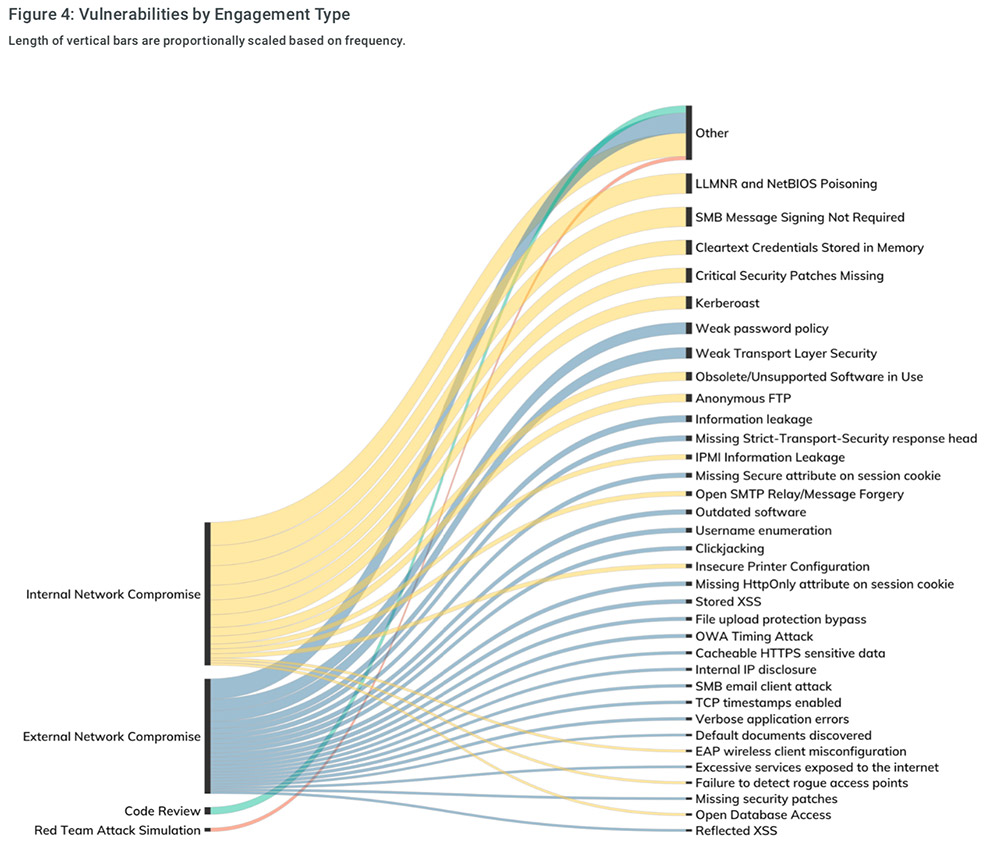
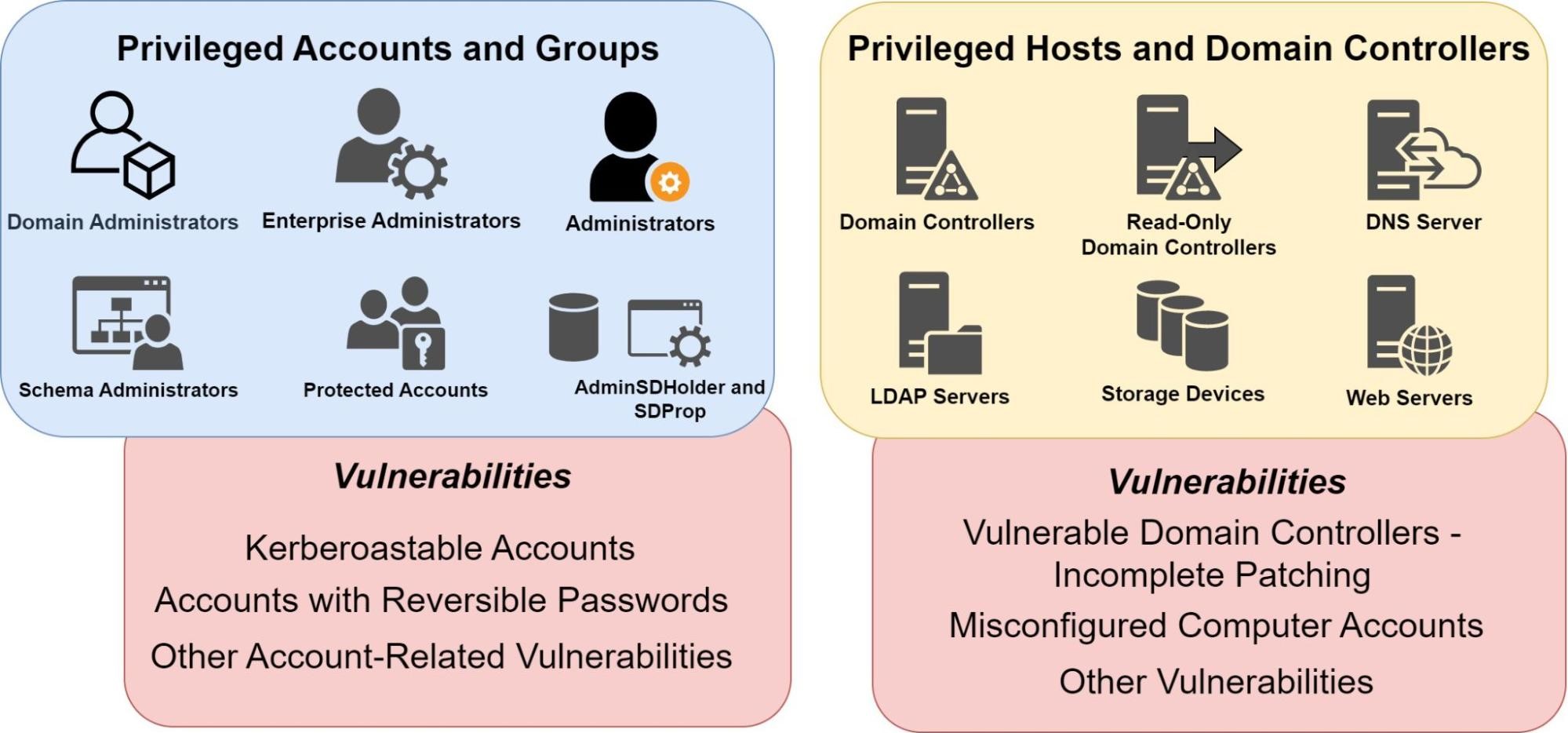
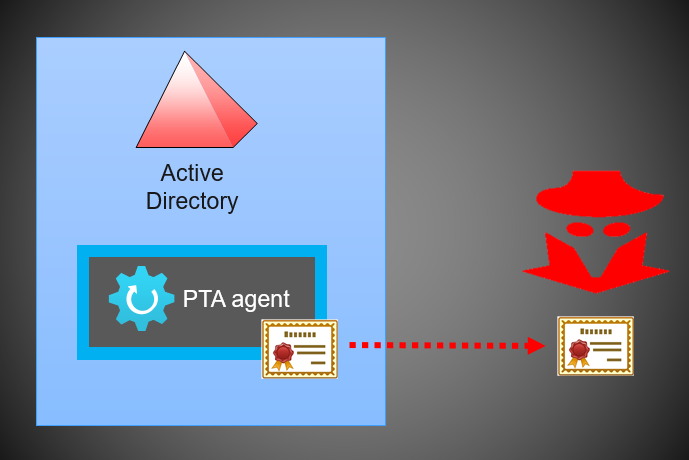
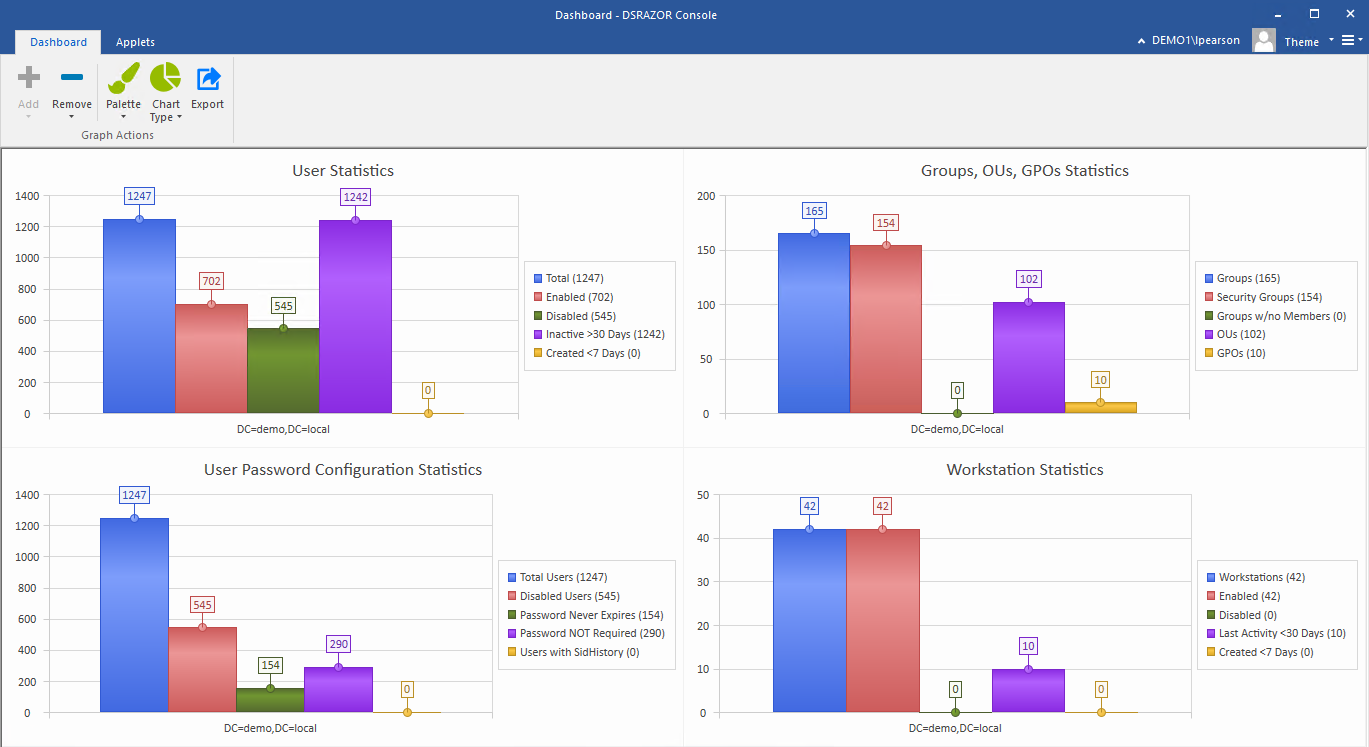
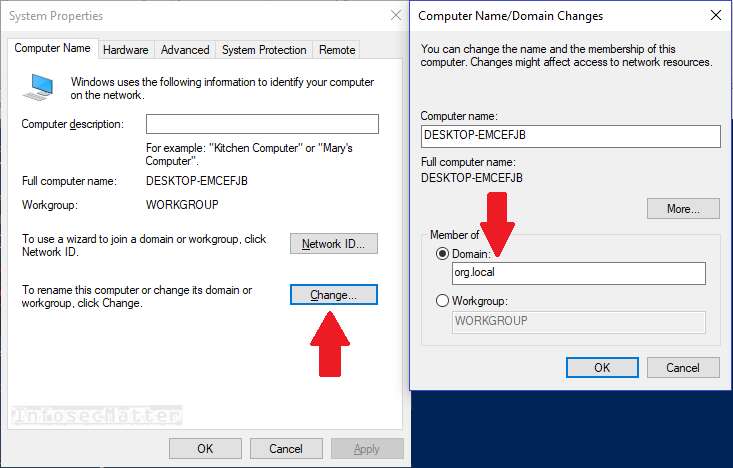
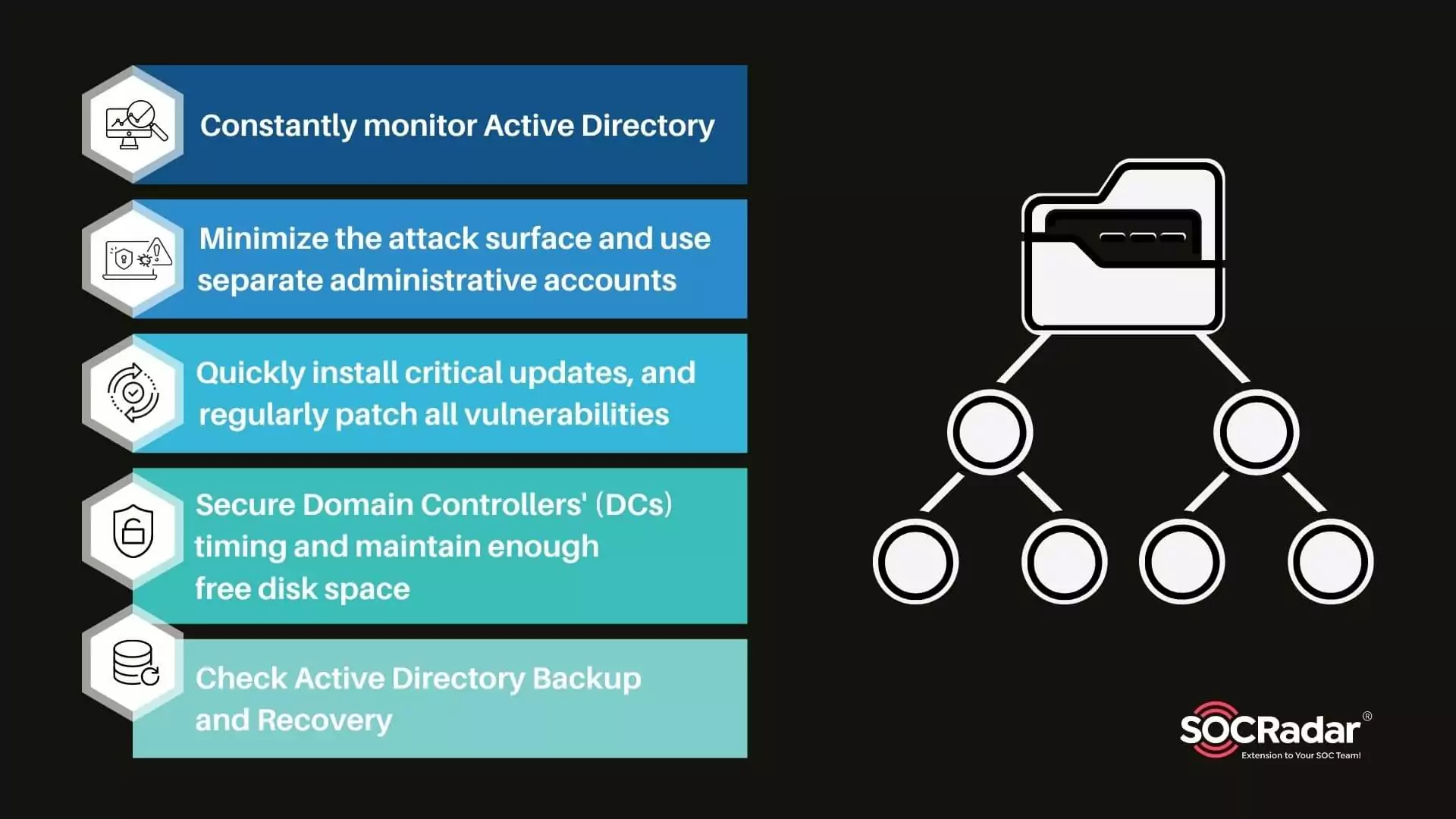
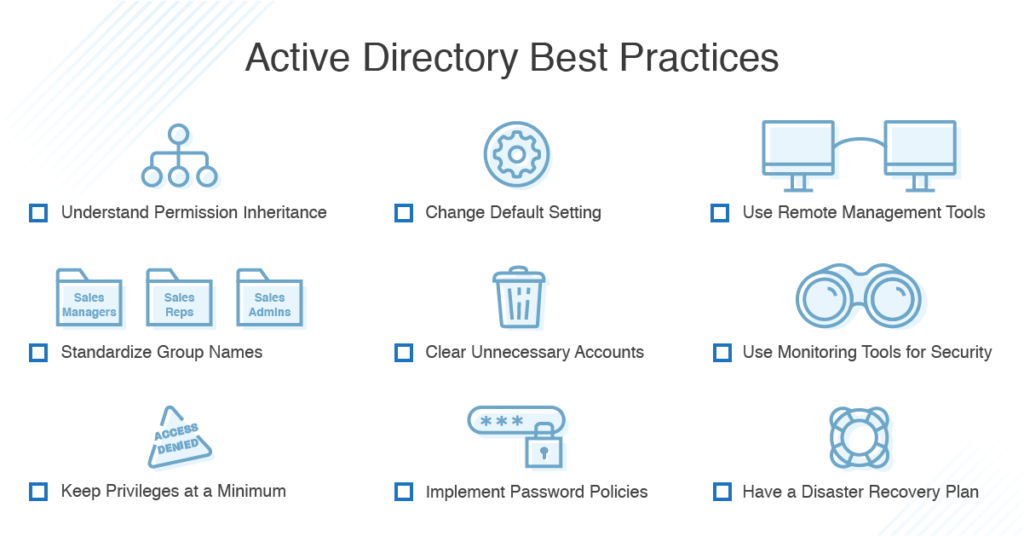
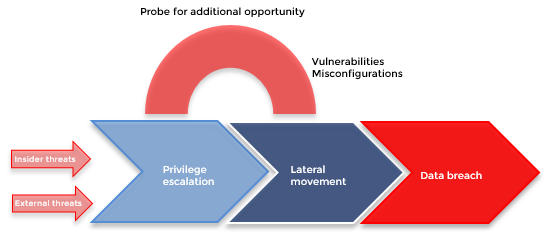
Three Active Directory vulnerabilities were addressed during Microsoft's January 2022 Patch Tuesday - The things that are better left unspoken

AD Attack Vectors: Top Active Directory Vulnerabilities eBook : Nafees, Muhammad, Arafat, Zahid, Ashraf, Nadeem: Amazon.in: Kindle Store